
WordPress powers millions of websites globally. It’s a preferred CMS for aspiring entrepreneurs and established businesses. Unfortunately, the popularity of the platform also makes it a tempting target for cybercriminals.
Although there are many advantages to using the platform, website owners must exercise caution when it comes to security. The good news is that you don’t need a huge investment or years of technical knowledge to secure your WordPress website.
Website security issues may evolve, but you can minimize the risks by embracing the standard security protocols. Something as simple as being aware of the looming threats significantly reduces the likelihood of your website being compromised, as you can easily take action against common security loopholes.
Keeping your website secure not only protects your sensitive business information but also your customer data. A compromised site severely affects your reputation and the trust you’ve built over the years.
In this guide, we will explore the ten common WordPress security problems and the viable fixes for each.
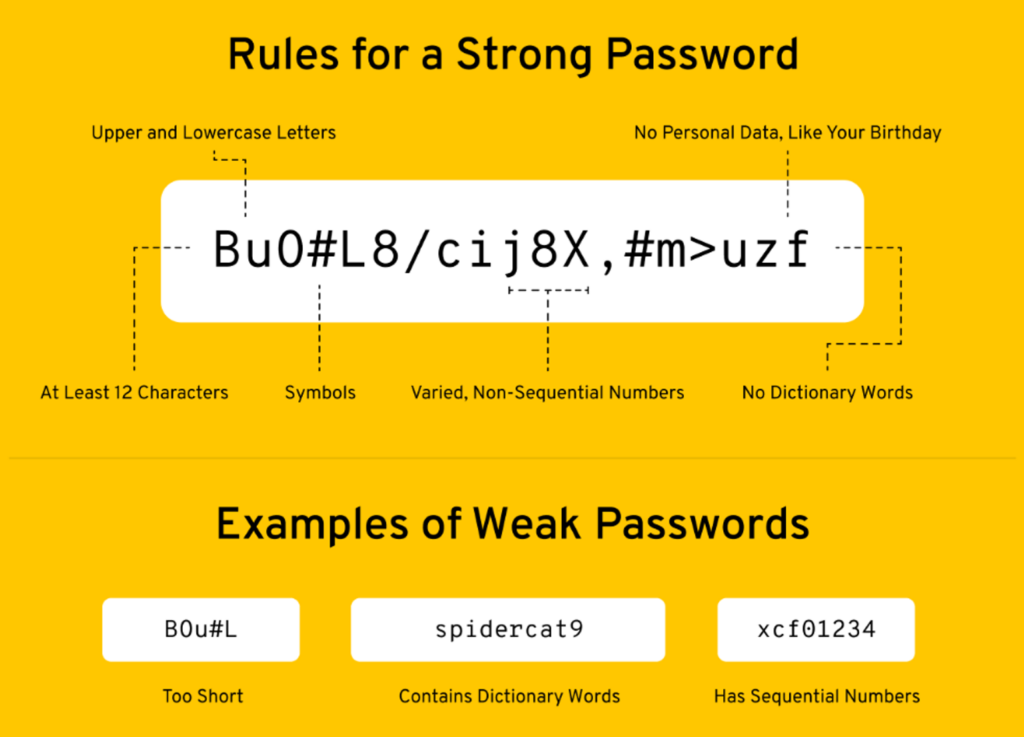
1. Weak Login Credentials
Weak login security procedures are often the cause of a WordPress website breach. You may find it convenient and harmless to settle for a short and easy-to-remember password, but it can turn out to be a huge security loophole.
To resolve this issue, you must always use a strong password, one that comprises uppercase and lowercase letters, along with numbers and special characters. Plus, website owners should constantly change their passwords to minimize the likelihood of a breach.
Just setting strong passwords isn’t enough. You must leverage two-factor authentication to strengthen your defense. Even when someone manages to obtain the login credentials, they still won’t be able to access your information with the secondary verification step in place.
You can also consider customizing your login URL to prevent automated attacks. Changing the default login path to the one you prefer makes it even more difficult for potential attackers to access your login page.
Another thing you should consider is limiting the number of failed login attempts. You must have an additional verification step in place in case you encounter failed login attempts from a particular IP address. By doing this, you prevent attacks where cybercriminals leverage automated systems to try different password combinations to hack into your website’s security.
2. Outdated WordPress Core
Using an outdated version of WordPress invites security threats to your website. A WordPress core update contains essential security patches that cater to the newly discovered vulnerabilities. Cybercriminals often target websites that have security flaws they can exploit. So, using an old version of WordPress instead of the new one is a risky move.
It’s more than just clicking the update button when you see the notification. There are many things that you may want to consider to keep the needle moving. You must have a periodic update schedule and proper website backup procedures in place prior to performing any updates.
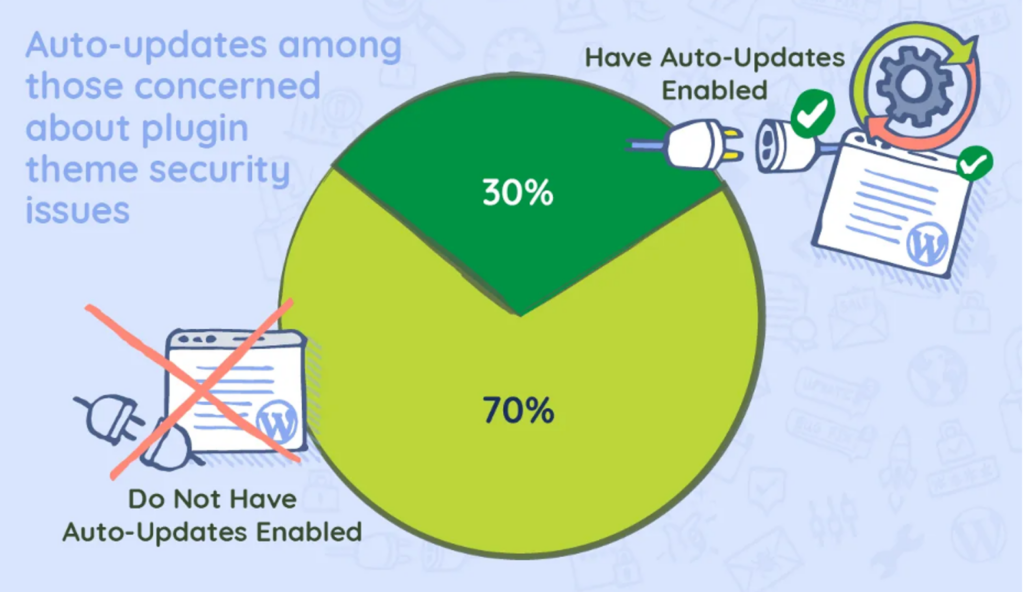
Setting up automatic updates for minor WordPress releases provides you with continuous protection against security threats. It ensures that you can access critical security patches as soon as they’re available. However, you should approach major updates with more caution.
You must also monitor your core files and look for any unauthorized changes that might indicate a security breach. You must understand which files belong in a standard WordPress installation to easily spot potential security issues. Leveraging file integrity monitoring solutions such as All-in-One WordPress Security and SolidWP may make things easy.
You must always test updates in a staging environment before applying them to your live site. It may seem like an extra step, but it ensures that you don’t break anything while performing an update. The functionality of your site matters just as much as its security.
3. Vulnerable Plugins and Themes
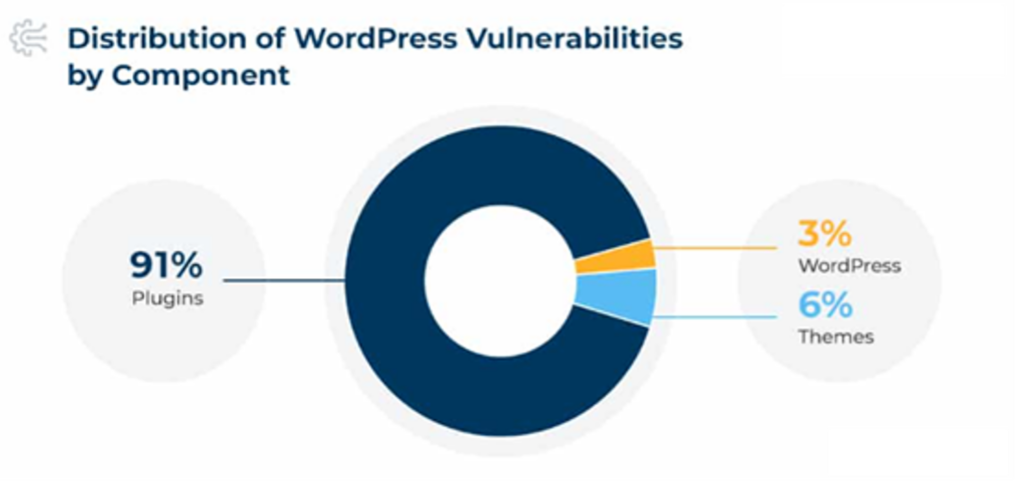
WordPress provides you with access to countless plugins and over 11,731 free themes. These tools not just boost your site’s functionality but also its aesthetic appeal. However, they’re still third-party components, and they may accompany various security vulnerabilities.
Outdated or poorly coded plugins and themes often contribute to website security breaches. Therefore, you must closely monitor such installations.
If the developers have forgotten about a particular plugin and it doesn’t serve a special purpose, it’s best to remove it from your site. Every installed plugin that you don’t need increases your site’s potential attack surface. Removing unnecessary plugins improves your website’s performance and security.
You must also download plugins from reputable sources only, such as the official WordPress repository or renowned commercial developers. Installing free plugins from unverified sources may contain malicious code or security loopholes. Even when installing premium plugins, you must research the developer’s security track record and update frequency.
Plugin behavior monitoring helps identify potential security issues before they become serious problems. You must keep an eye on unusual activities, such as unexpected database queries, file modifications, or your site’s performance fluctuations.
4. Permission Issues
Always be wary of who can access your files. Only authorized personnel should have permission to access or make modifications to the files on your website. If you’re not careful, unauthorized personnel can inject malicious code and compromise the entire system.
Different files and directories require varying levels of access. Generally, your core files should be read-only. You should never allow anyone to make modifications to them. However, directories encompassing uploads or plugin installations may be an entirely different story. You can’t be too restrictive to compromise your site’s functionality, nor too lenient to cause security vulnerabilities.
Directory access control extends beyond basic read-write permissions. Protecting sensitive directories from direct browser access helps prevent unauthorized users from viewing your file structure or accessing configuration files.
It’s best to conduct periodic file permission audits to improve your site’s security. Core updates, installations, and routine maintenance can change file permissions without you knowing. Therefore, you must be aware of such changes to keep your website’s security intact.
5. SQL Injection Issues
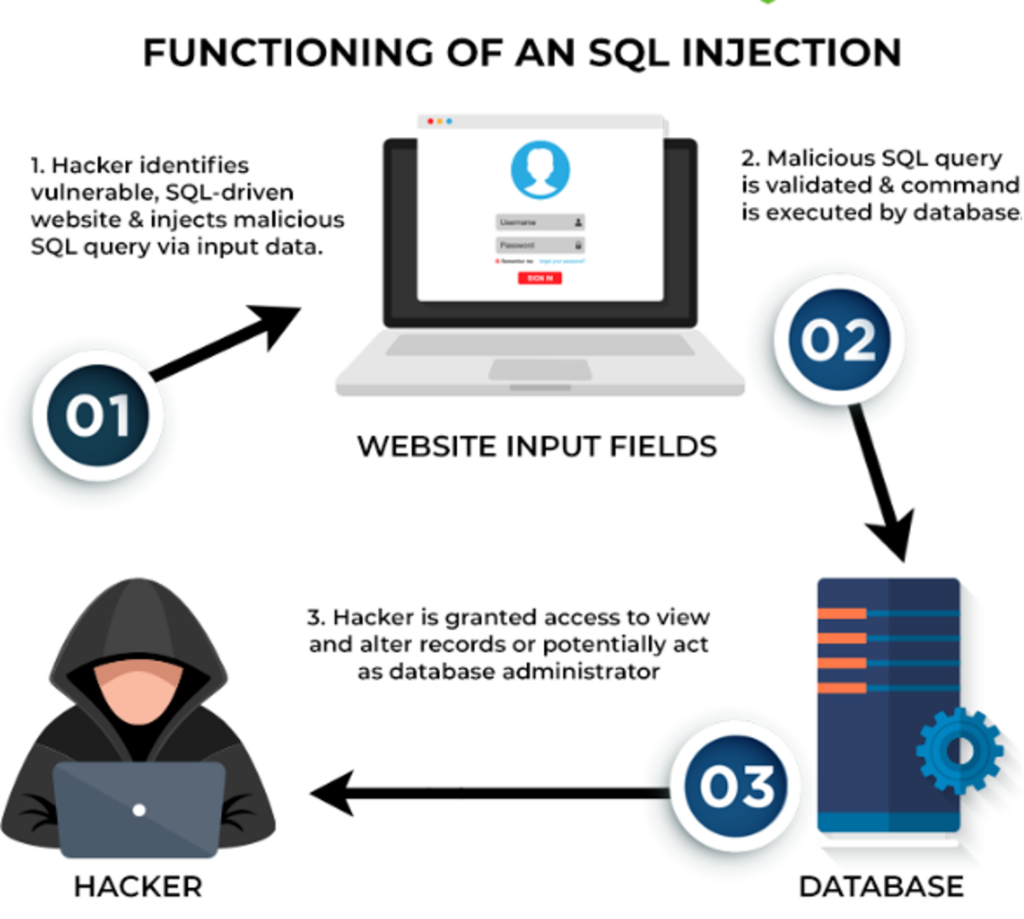
SQL injection is one of the most critical threats to your website’s security, potentially exposing your entire database to unauthorized access. These attacks occur when someone inserts a malicious SQL code into your site’s database. A successful SQL injection attack may cause data theft, content manipulation, or, in some cases, complete database corruption.
To prevent this, you must ensure that every piece of data that enters your WordPress database is clean and verified before processing. WordPress provides you with built-in data sanitization capabilities, but custom code requires careful attention.
Regular database maintenance serves as a viable fix. You should periodically remove unnecessary data, optimize tables, and ensure proper index structures. You must also carefully evaluate database access permissions to minimize the likelihood of a security breach.
6. Cross-Site Scripting Problems
Cross-site scripting enables cybercriminals to inject malicious JavaScript code into your site’s pages. The moment your visitors’ browsers process this script, they may fall victim to data theft or get redirected to malicious sites. So, such attacks critically damage your reputation and the trust you’ve built over the years.
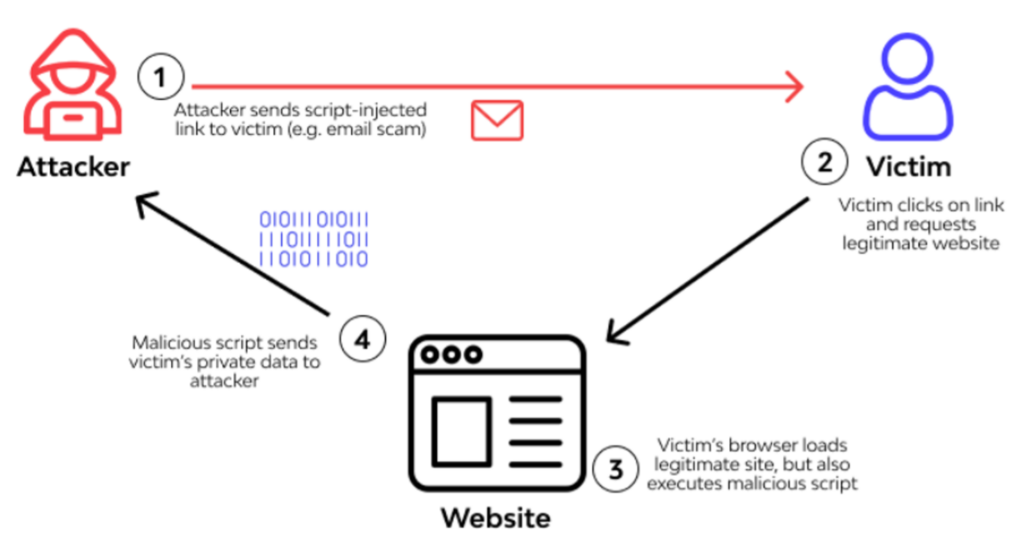
A proper implementation of HTTP security headers acts as your first line of defense. They prevent malicious scripts from executing. Content filtering also comes in handy in improving your site’s security. You should monitor user-generated content, form submissions, and even URL parameters.
Any method through which data enters your site needs proper evaluation to prevent script injection. Proper data input validation helps prevent many common XSS attacks while ensuring overall data quality.
7. Malware and Backdoors
Malware attacks are a common occurrence. Cybercriminals target vulnerable sites to inject spam links or content to steal user data. They may also create backdoors for future attacks. They often exploit outdated plugins, themes, or other software components to carry out such attacks.
File integrity scanning serves as a viable fix that prevents malware attacks and backdoors. As we discussed above, you search for unauthorized changes that may indicate an infiltration. Leveraging a security plugin serves as a viable countermeasure. The tool operates in the background and alerts you when it detects potential threats.
You can also prevent such attacks by sticking to the coding best practices and maintaining clean installation files. It helps prevent vulnerabilities that potential attackers can exploit. You must also have a data recovery plan in motion to cope with the worst-case scenario. You must periodically create a complete backup of your site and document any custom configurations.
8. Brute Force Attacks
Brute force attacks encompass automated password attempts. These attacks threaten your website’s security and affect its performance by consuming server resources. You shouldn’t take such attacks lightly. Even if it takes a million failed attempts, attackers only need to guess the right credentials once.
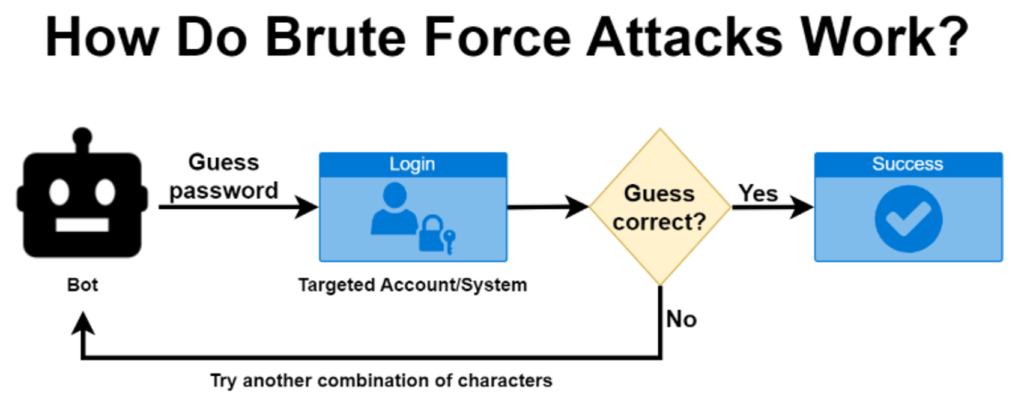
Limiting failed login attempts may serve as a viable strategy. You can also consider temporarily or permanently blocking the IP representing the attempts. Implementing CAPTCHA is also a wise move to prevent brute-force attacks. However, it can cripple the user experience at times.
You should leverage CAPTCHA systems that complement your website security without having to compromise the experience you offer. CAPTCHA is an additional authentication step that prevents automated tools from trying different password combinations.
You must maintain detailed logs of all login attempts. Reviewing the logs may help you identify potential security issues before they cause critical damage.
9. Insecure Hosting Environment
A reliable hosting environment plays a key role in keeping your website safe. No matter how many protective measures you implement, an insecure hosting environment often creates vulnerabilities for potential attackers to exploit.
A few of the issues you may end up grappling with if you choose a subpar hosting service are outdated server software, poor server configurations, and improper isolation between hosting accounts.
So, go for one that offers regular server updates, a built-in firewall, secure PHP configurations, and robust monitoring. Other essential features may include SSL certificates, automated backups, and malware scanning tools.
A reliable hosting service may cost more than the cheap alternatives you may find. However, the damages caused by security breaches may end up costing you a lot more. A secure hosting foundation paired with the recommended WordPress security measures will help you create an impenetrable structure.
Final Thoughts
There you have it: the nine common WordPress security issues and how you can fix them. We covered all the noteworthy security problems that you may encounter when managing a WordPress site.
Protecting your WordPress website from potential dangers may seem overwhelming, especially when you have just gotten started. That’s why we decided to educate you about the potential issues you may encounter and recommend viable solutions.
Our recommendations will protect your site against common threats while keeping its functionality intact. Just remember that keeping your website secure isn’t a one-time activity but rather an ongoing process.
