
If you’ve spent any time looking into web hosting, server management, or WordPress development, you’ve probably run into the acronym SSH. It pops up in hosting dashboards, developer guides, and just about every conversation about server security. But what is SSH, really? And why does it matter for you?
Here’s the short version: SSH stands for Secure Shell, and it’s a way to communicate with a remote computer securely. Rather than logging in to your server through a web-based control panel, SSH lets you connect directly through a text-based interface called a terminal. Every command you send and every response you receive is encrypted, which means nobody eavesdropping on your network can see what you’re doing.
If you’ve never opened a terminal before, this might sound a bit intimidating. Don’t worry, that’s normal. This article isn’t about memorizing commands. Instead, we’ll break down what SSH is, where it came from, how it works in simple terms, and how it fits with tools like SFTP. Think of this as the background you need before you dive into a hands-on tutorial.
The Birth of SSH
The Problem with Plaintext
To see why SSH is important, it helps to look at what came before. Back in the early days of networked computers, people used tools like Telnet and rlogin to access remote servers. These tools got the job done, allowing you to type commands on your computer and have them run on a server far away. But there was a big problem: everything, including your username and password, was sent in plain text. Anyone who could see the network traffic between you and the server could read every keystroke.
For a while, this didn’t seem like a big deal. Early networks were small, mostly used by universities and researchers, and people trusted each other. But as the internet grew and more people got online, that trust started to break down. By 1995, password sniffers posed a real threat to university networks.
Tatu Ylönen’s Solution
That’s exactly the scenario that prompted Tatu Ylönen, a researcher at the Helsinki University of Technology in Finland, to create SSH in 1995. After a password-sniffing attack hit his university’s network, Ylönen wrote the first version of the SSH protocol as a direct response. The core idea was simple but powerful: encrypt the entire session from the moment of connection, so that credentials and data alike are protected in transit.
The first version, called SSH-1, was released as free software and quickly caught on. In just a few years, it replaced Telnet and rlogin for most remote server work. Ylönen went on to start a company around SSH, and the protocol itself improved over time. SSH-2 came next, fixing security issues and making things more robust. These days, when people talk about SSH, they almost always mean SSH-2. The most popular version is OpenSSH, which is open source and maintained by the OpenBSD team.
Understanding SSH
The Lock-and-Key Analogy
SSH security is built on something called public-key cryptography, which is actually easier to understand than it sounds. Picture this: you have a special padlock and a key. You can hand out copies of the padlock to anyone (hosting company, coworker, client), but you keep the only key that opens it. If someone wants to send you something securely, they lock it with your padlock. Only you, with your key, can open it.
In SSH, the padlock is your public key, and it sits on the server. The key in your pocket is your private key, and it always stays on your own computer. When you connect with SSH, your computer and the server use these keys to prove who they are and set up an encrypted connection. Your private key never leaves your machine, which is a big part of what makes SSH so secure.
What Happens When You Connect
Let’s skip the math and look at what actually happens when you connect with SSH. First, your computer reaches out to the server, and they agree on how they’ll encrypt the connection, like picking a language they both understand. Then, the server proves who it is by showing its public key, and your computer checks if it’s on the list of trusted servers. Finally, you prove who you are, either by using your private key (the best way) or by entering a password.
Once both sides are happy, a secure tunnel is set up. From then on, everything you send or receive is encrypted. You can type commands, move files, or even send other types of network traffic through that connection, and it’s all protected from prying eyes.
Why This Matters for WordPress
If you manage WordPress sites, SSH gives you direct access to your server’s operating system. You can manage files, run database commands, update plugins or themes, and fix problems without needing to log in to a web dashboard. Tools like WP-CLI (the official command-line tool for WordPress) are designed to work over SSH, and they make everyday tasks much faster than clicking around in wp-admin.
But it’s not just about speed, SSH is also more secure. When you log in to your hosting control panel in a browser, you have to trust that the web interface is safe, your session can’t be hijacked, and no one is watching on public Wi-Fi. With SSH and key-based login, you avoid most of these worries. There’s no password to steal, no session token to grab, and the encrypted tunnel is set up before any sensitive info is sent.
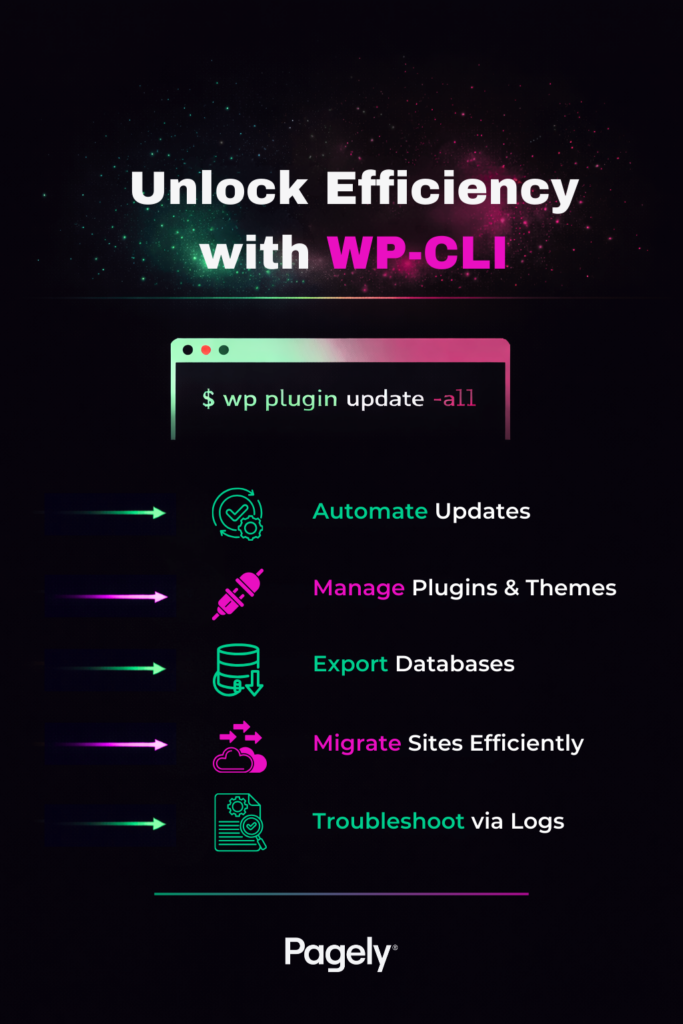
SSH and SFTP
What SFTP Actually Is
You’ve probably heard of SFTP, too. It stands for SSH File Transfer Protocol (sometimes called Secure File Transfer Protocol). Even though it sounds like just a secure version of FTP, SFTP is actually a different protocol that runs over SSH. That difference is important.
The original FTP protocol was created in the 1970s and didn’t use any encryption. Your files, username, and password were all sent in plain text. FTPS (FTP Secure) added encryption later, but it also made things more complicated with certificates and port settings. SFTP does things differently: it uses the SSH connection you already set up and lets you transfer files through that same encrypted tunnel. One protocol, one port, one login.
When You’d Use Each
In practice, SSH and SFTP often go hand in hand. You’ll use SSH when you want to interact with your server in real time, like running commands, reading logs, restarting services, or managing WordPress via WP-CLI. You’ll use SFTP when you need to transfer files between your local machine and the server. This includes uploading a theme, downloading a backup, or replacing a configuration file.
Many popular applications support SFTP natively. Tools like FileZilla, Cyberduck, and Transmit all offer graphical drag-and-drop interfaces for SFTP, which makes file management accessible even if you’re not comfortable in a terminal. The key takeaway is that both SSH and SFTP rely on the same underlying encryption and authentication.
Learning Resources
One of the great things about SSH is that it’s been around for nearly thirty years, so there’s a huge amount of learning material out there. Here are some good places to start, depending on how you like to learn.
Official Documentation and Guides
The OpenSSH project maintains thorough manual pages for every component of the SSH suite. They’re technical, but they’re also the definitive reference. If you’re a WordPress developer specifically, the WP-CLI handbook covers everything you need to know about running WordPress from the command line once you’re connected. And if you’re hosting with Pagely, see our step-by-step walkthrough on getting started with SSH.
Interactive Practice
Reading about SSH only takes you so far; the real learning happens when you start connecting to something. Many hosting providers offer staging environments where you can experiment safely. Alternatively, services like OverTheWire’s Bandit wargame teach Linux command-line fundamentals through a series of puzzles that you access over SSH. It’s a surprisingly fun way to build terminal confidence without any risk to a production site.
Going Deeper
Once you’re comfortable with the basics, you might explore topics like SSH tunneling (forwarding traffic from one port to another securely), SSH agent forwarding (so you don’t have to copy private keys to intermediate servers), or configuration hardening (disabling password authentication entirely, changing default ports, setting up fail2ban to block brute-force attempts). Each of these topics has a wealth of guides and community discussion around it.
The important thing is to start. SSH is one of those skills that feels foreign for about fifteen minutes and then quickly becomes second nature. And once it clicks, you’ll have a foundational tool that makes every other aspect of server management faster, safer, and more transparent.
Looking for a managed WordPress host where SSH and WP-CLI are first-class citizens? Our Managed Hosting for WordPress is built for developers who want real control over their hosting environment.

