WordPress Security has gotten a lot of press (pun intended) of late. Every 3rd day there is new post, or guest post by someone driving home the importance of securing your WordPress install with proper file permissions, choosing strong passwords, and the like. Listen to them, and take heed as they are smart people telling you what you should be doing.
Our point of view is that security starts with us, the hosting provider. To that end we have made choices and implemented things that we feel backup our claim of being the most secure WordPress Hosting outfit available. When something is as important as this, it needs to be more than just hype.
We have always been transparent about how we do things. So allow me to share some more.
Securing Pagely client sites
We do a number of things that we feel are in the best interest of our clients. Some things we have talked about in the past, others we have not made much of a fuss over.
Automatic Core Updates
If you host with us, you are always running the latest version of WordPress. Except for the 1-3 week lag time between a major release like 3.4 to 3.4.1, there are no exceptions to this, for any client. If you are curious why we wait a little time between major releases you can read it here. Forcing every instance to be current, eliminates the problem of your site running an outdated version. For as secure as WordPress is, they still push security updates to address issues as they come up.
Automatic Plugin Updates
If you host with us, your plugins are updated automatically every 3-4 weeks. Again this is to eliminate old plugins with possible security problems affecting your site.
Introducing Maid Service
Don’t we all love hotels? You leave the room in the morning with disheveled bed and breakfast dishes on the table, and come back in the afternoon to a tidy and clean room. We have recently turned on a new automated service we call “the maid”. It is a worker program that scans through every site periodically and cleans up after you. The maid does the following things:
- Scans and resets all file permissions to proper values
- Updates all plugins
- Removes any banned plugins. (Yes we ban a few, mostly backup and stats plugins and it is for your own good)
- Creates an incremental backup of your site files, and full backup of your database.
- Scans your site for outdated timthumb scripts and replaces them.
- Removes any files that don’t belong. This could be a number of things like __MACOSX folders.
- Sunsets ftp passwords
- among other things… (we’ll be turning on the ‘cold storage’ of inactive plugins and themes down the road)
Currently the maids actions are all logged to our system where only we can see it. In the near future these status messages will be shown on your Atomic panel and you will also receive a short email message if the maid found anything to act on.
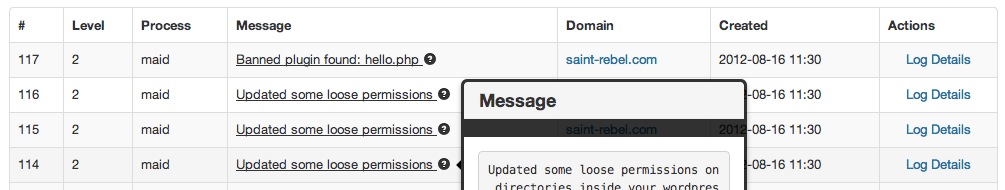
The maids only job is keep your site safe and secure and it works for free.
Malware Scanning and Remediation
Let us start by saying, we love Sucuri and if you don’t host with us, you better be using their service. They are pros at what they do. However, no one is able to scan your site and detect problems as good as your hosting service, our in house services and the service Sucuri provides overlap, and in may areas we are simply able to do more. We scan every file with multiple signature based scanning programs such as Savscan and Maldet. In addition to that we have written a suite of custom match patterns for detecting things that these automated scans miss, and yes they do miss things from time to time. Our system, and real humans proactively quarantine the bad stuff and repair your site to proper working order.
Malware happens. For a long time page.ly never had a instance of malware, then timthumb happened and we have to deal with it like everyone else.. or not, well more on that later.
Enterprise Grade Firewalls and DDoS protection
This is where page.ly sets the standard above all others. We stop more potential attacks before it even gets to your site than we think our competitors even know they are being targeted with, ignorance is bliss as they say. DDoS attacks stop in their tracks, not after days.. but in seconds.
Due to our unique partnership with Firehost, we not only gain the benefit of their enterprise grade security hardware at the network edge, we also work closely with them identifying and blocking attacks with a custom rule set.
This pie chart of blocked attacks is generated over the last 15 days.
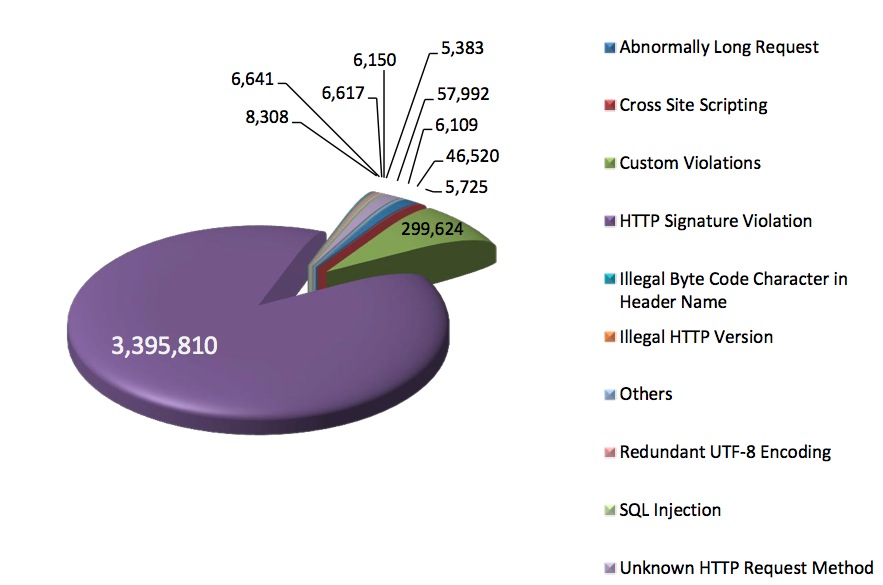
Here is the cool part The 299,624 number in dark green marked Custom Violations: Those are malicious requests that page.ly blocks above and beyond the rule set provided by our redundant Imperva Web Application Firewalls. Those requests are being blocked by rules we created and implemented based on analysis of the millions of requests we see each month, and let me assure they are some NASTY shit. Props to Firehost for being on the same page as us and making Security a core of their business.
Here is a 1 day view from a different logging source.
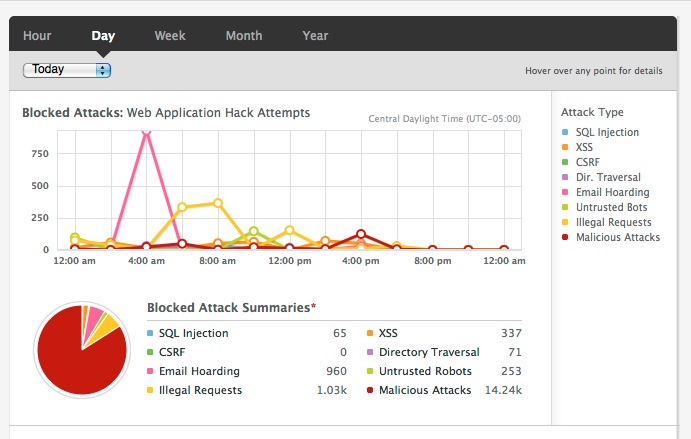
Bottom line, no one can match this level of network security. Protection does not stop at the network edge. There are internal firewalls between the mysql and webnodes, web nodes and memcache, mysql and the file system, etc.
Varnish security.vcl, Suhosin, and more.
We run a customized version of this great app on our varnish nodes that add an additional level of security to all network traffic. The web nodes all run a hardened Suhosin php instance, with clean separation between accounts and user permissions. Further hardening extends to all systems that we feel add additional layers of protection.
And then there is timthumb..
Ahh timthumb.. you nasty devil. Here’s how the exploit works. A bot scans your site for vulnerable timthumb scripts (found in many many themes and plugins) and requests an external url source. That source is actually a nasty payload that will install in most cases some malware that injects iframes and in some cases php shells and other shenanigans into your site. So how do you stop it? Patch timthumb and disallow external sources. But what about the thousands of our clients that use it and all their links that look like ../timthumb.php?src=http://somedomain.com/..? We can’t just ask them to all modify their themes/plugins/sites. We disallow all external timthumb requests yet let our customers carry on their merry way without having to modify any links. Not only do we patch all old timthumb files, we block the vector of attack out at the network edge before it even reaches your site. You are welcome.
The competitors marketing hype.
Visting the websites of the other WordPress Hosting providers you would come away thinking everyone is this secure.
Competitor 1: Uses Rackspace to host their sites. You may have used rackspace, and have never seen them offer any sort of additional protection on their servers other than what you configure yourself. A decent firewall appliance costs hundreds of thousands of dollars, if Rackspace is not providing it, is the competitor springing for it on their own dime? How would they install it in the cloud they dont control? UPDATE: The answer is yes, they are running a firewall they do pay for themselves in addition to the private Rackspace setup. Kudos to them.
Competitor 2: Uses Linode and other budget VPS providers Peer 1/ServerBeach bare-metal. The Linode feature list makes no mention of enterprise firewall appliances. They do however mention they run software firewalls on “high-end/custom” plans. This competitor offers a security guarantee to clean up the mess after it happens. They would have to if they have no means of preventing one they are not doing a great job at preventing it according to a handful of their customers.
Competitor 3: Uses Media Temple. Now we actually really like media temple. But for as much as we admire them, they run the same wide open network as everyone else and leave it up to the customer to harden the nodes as best they can.
If you want to see more, have a look here on the right side and read those posts by Sucuri, whom so happens to be contracted by many of these competitors to clean up attacks after the fact. But the Sucuri service does NOT extend to prevention at the server or network level. It appears these competitors claim the mantle of security, but do not emphasize prevention and outsource the cleanup to a 3rd party.
The Trade off
The levels of network and server security that we subject our system to has some small trade offs. In some cases requests may be slowed a hundredth of a second as they are processed through our firewalls and hardened php servers. This is imperceptible in most cases and request times are still 50-80 milliseconds. Sometimes our clients may get a frustrated when posting javascript directly into the tinymce editor and our firewall blocks the POST. These are small tradeoffs we will accept for the greater good of keeping all clients as safe as we can.
“Secure” is how we do business.
No service is 100% secure. It is a fallacy to think it ever could be. However making our system as secure as it can be is the lofty goal that we aim for everyday. Problems do happen and we do our best to address them and take proactive measures to prevent them from happening in the future. We had some issues with timthumb like everyone else. We did our best to patch the files when the outbreak first hit, but missed many that resulted in some cleanup. We tuned our system and firewalls up since then and have been trouble free for some time in this regard.
Listen to the blog posts you read, choose good strong passwords, don’t ever use 777 permissions, and most of all, choose a solid WordPress Hosting provider that demonstrates to you how they secure your site and goes beyond the marketing hype to make security a core part of their business.
