
Introduction to Cybersecurity Threats
It’s every system administrator’s worst nightmare. Hackers gain access to your system, stealing mission-critical information, locking sensitive files, or leaking proprietary information to the public.
Frankly, it can be hard for companies to recover from such an attack. The data breach at Equifax in 2017 is turning out to be one of the most costly in history, costing the company upwards $275 million.
And even if the consequences aren’t that high for your company, you can be sure that you won’t escape unscathed. Whether it’s a damaged reputation, lost data, or even federal sanctions, cyber attacks are tremendously destructive.
But not all cyber attacks are the same. They utilize different methods to achieve different ends, and as such, require different prevention strategies.
Cyber Attacks to Look Out for
Here are the top six cyber attacks you need to be ready for in 2024.
Cyber Attack #1: Ransomware
This is as scary as it sounds. Ransomware is, essentially, the digital version of kidnapping. It works something like this.
A hacker manages to get a ransomware file onto your servers. Typically, hackers will use some form of phishing, in which a user in your system receives an email with a malicious file attached. Of course, this file doesn’t look malicious. It looks completely legitimate, like something they receive every day.
When the user opens the file, the ransomware file is deployed, encrypting and locking specific, highly sensitive files on the user’s computer or your servers. When the user attempts to open the files, they are confronted with a message stating that their files have been locked, and that they will only receive the encryption key if they pay a specified amount to the hacker, usually through an untraceable Bitcoin payment.
This type of attack is massively on the rise, with ransomware attacks growing 2,502% in 2017.
Who is at risk for ransomware attacks? While there’s a sense in which everyone is at risk, hackers often target organizations that need quick access to their files, such as medical facilities or government agencies.
The effects of a ransomware attack can be crippling. As David Bisson at Tripwire notes:
On 26 July 2017, Arkansas Oral & Facial Surgery Center suffered an attack at the hands of an unknown ransomware. The incident didn’t affect its patient database. However, it did affect imaging files like X-rays along with other documents such as email attachments. It also rendered patient data pertaining to appointments that occurred three weeks prior to the attack inaccessible.
At the time of discovery in September 2017, Arkansas Oral & Facial Surgery could not determine whether the ransomware attackers accessed any patients’ personal or medical data. It therefore decided to notify 128,000 customers of the attack and set them up with a year of free credit-monitoring services.
Unfortunately, a ransomware attack places an organization between a rock and a really, really hard place. They can pay the ransom to release their files, but that will mean instant bad publicity for them and the widespread knowledge that they’re willing to pay for locked files. If they refuse to pay, they may lose business-critical files, which can also cost them enormous sums of money.
Cyber Attack #2: Internet of Things
The Internet of Things is made up of all the digitally connected items that, in the past, have never been able to connect to the internet. We’re talking appliances, thermostats, cars, and thousands of other things. And while these smart home innovations can certainly make life easier, they also make your company much more vulnerable to attack.
The unfortunate reality is that many IoT devices are riddled with security holes which smart hackers can slip through, usually without notice. And if hundreds of IoT devices can be coordinated for an attack, it can create chaos and catastrophe on an enormous scale.
In 2016, a coordinated IoT attack was launched that resulted in huge portions of the internet simply being inaccessible. Sites from HBO to Etsy to Fox News and PayPal were affected, and eventually led to an investigation by the Department of Homeland Security.
This problem isn’t going anywhere and presents a significant threat to your company, especially as more IoT devices are incorporated into your network.
As Greg Nichols noted in ZDNet in March of 2018:
The average number of IoT devices in the workplace is expected to increase by nearly 9,000 to an average of 24,762 devices.
97 percent of respondents [to a survey] say an attack related to unsecured IoT devices could be catastrophic for their organization and 60 percent are concerned the IoT ecosystem is vulnerable to a ransomware attack.
81 percent say that a data breach caused by an unsecured IoT device is likely to occur in the next 24 months.
Only 28 percent say they currently include IoT-related risk as part of the third-party due diligence.
These are staggering numbers and indicate just how large this problem is. Expect this to be one of the prime areas targeted by hackers in the next few years.
Cyber Attack #3: Social Engineering and Phishing
These hacker methods sound as old school as they are, but they likely aren’t going anywhere. Why do they still work? Because they rely solely on people. Social engineering and phishing involve hackers posing as legitimate institutions in order to trick people into entering sensitive information.
For example, a hacker may email employees at your company, posing as a system administrator, asking them to reset their password. A link is included in the email that directs the employees to a page that looks like one of your legitimate password reset pages, including fields for the username and old password. When the employee enters their old password, the hacker gets access to what is actually their current password. They can then immediately log into your system without any detection.
These types of attacks are getting increasingly sophisticated. For example, hackers often launch these attacks in the wake of legitimate security breaches. People who would normally never fall for such a scam are much more liable because they know there was a security breach and that password resets are standard protocol following a breach.
The stats indicate that phishing isn’t going anywhere. Dashlane notes::
- Phishing attempts rose 65% in 2017.
- 76% of businesses reported being the victims of a phishing attack.
- Phishing rates are increasing across all industries, meaning no business is immune.
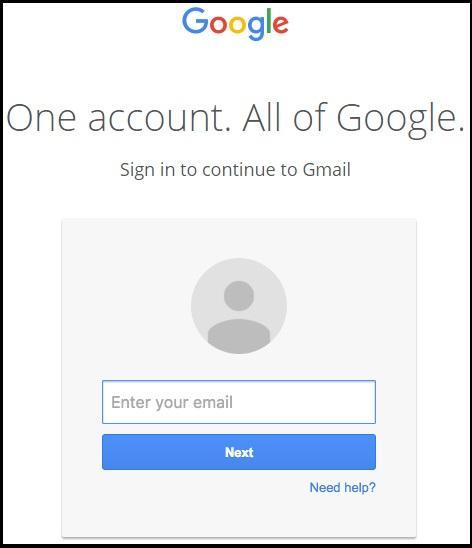
This is an example of a 2017 phishing scam that hit nearly 1 billion Gmail users. It looks like a Google sign in, but imputing your data would give hackers access to your Gmail. These types of attacks will continue simply because humans don’t change. There will always be ways to deceive people into giving up sensitive information, no matter how many measures are put into place.
Cyber Attack #4: Cracking
Cracking is when hackers use high-powered computer programs to systematically enter millions of potential passwords in the hope of “cracking” some of the easier ones.
And we all know that millions of people still use laughably simple passwords, including the ones they use to log in to your system. We’re talking passwords like:
- “Password”
- “Abc123”
- “111111”
- Their own name
- Their birthday
A recent study showed that a staggering 35% of people have what are considered to be “weak” passwords. These are easily crackable passwords and most of the other 65% use passwords that can also be cracked, given enough time.
As computers grow increasingly more powerful, cracking programs can quickly generate billions of potential passwords to try. If passwords aren’t sophisticated enough (i.e. they don’t contain enough random characters), they can still be somewhat easily cracked.
And while system administrators are increasingly forcing users to devise more complicated passcodes, cracking attacks will always be a danger until users are forced to create completely unique passcodes that are very difficult to crack.
Cyber Attack #5: Man In The Middle
Man in the middle attacks happen when one of your employees conducts company business on an unsecured wireless network. For example, let’s say an employee is traveling and they stop in a coffee shop to catch up on a bit of work.
If the wifi in the coffeeshop is unsecured, a hacker may be able to intercept any information being sent from the employee’s computer. This could include passwords, sensitive emails, contact information, and anything else they might transmit over the network.
While there are certainly precautions that can be taken against this, such as installing VPN software on employee computers, there’s still the risk of information being captured from personal devices, such as tablets and mobile phones.
Cyber Attack #6: WordPress Specific Attacks
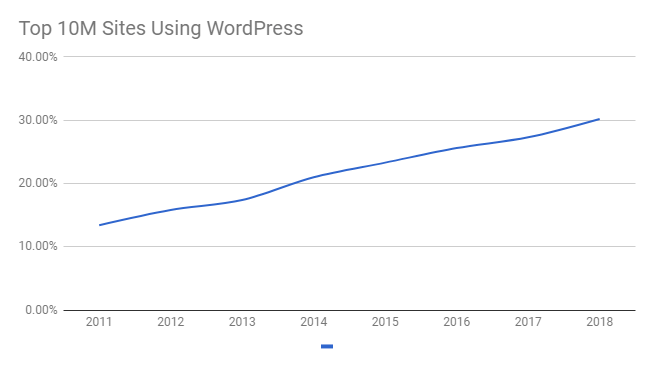
Given that WordPress powers approximately 30% of the internet, it should come as no surprise that WordPress security attacks are increasing in number. WordPress is generally secure out of the box, but as a site gains more traffic and notoriety, hackers will resort to increasingly sophisticated methods to take down WordPress sites.
[WordPress Usage Growth by Year Graph]
One area of particular vulnerability is third-party plugins. If these aren’t updated on a regular basis, they can introduce risks to your system. A recent study by Securi noted that 25% of hacked WordPress sites were exploited because of out-of-date plugins.
Additionally, WordPress sites that don’t use SSL certificates are vulnerable when being accessed through unsecured networks. Hackers on the networks can use Man In The Middle attacks to sniff out login details, then login into the site and deface it.
Finally, failing to disable pingbacks can put your site squarely in the middle of a DDoS botnet.
As WordPress continues to expand its reach, it will be increasingly important to lock down sites against attacks directed specifically at the platform.
What Should You Do?
There are a number of basic precautions that can and should be taken regarding security, such as regularly training employees on the basics of security, forcing employees to use VPNs on all work related devices, implementing the latest security software, etc.
However, as the threat of cyberattacks grows, you should also consider more sophisticated measures such as secure WordPress hosting. If you truly want to protect your company, you’re going to want to utilize such techniques as a dynamic web application firewall, chroot user separation, real-time malware scanning, and full restoration processes in the event of a breach.
Moreover, in the face of these evolving threats, it’s essential to stay ahead of the curve by keeping abreast of the latest cybersecurity trends and threats. This proactive approach can help you anticipate potential vulnerabilities and take preemptive action to mitigate risks. It’s not just about the immediate steps you take, but also about fostering a culture of security within your organization. This means going beyond the basics and integrating security awareness into every aspect of your business operations.
When it comes to web security, don’t settle for half-measures. When they fail, the costs are enormous and you’re left to pick up the pieces.
Additional content (add what you see relevant)
Looking Ahead: Preparing for 2024
As we move towards 2024, the landscape of cybersecurity is rapidly evolving. With advancements in technology and the increasing sophistication of cybercriminals, it’s crucial to stay one step ahead. Here are some forward-looking insights and protective measures to consider:
AI and Machine Learning in Cybersecurity: Leveraging artificial intelligence and machine learning can dramatically enhance your security posture. These technologies can predict and identify potential threats before they manifest, providing an additional layer of defense.
Zero Trust Architecture: Adopting a zero-trust security model, which assumes that threats could be internal or external and verifies every access request regardless of location, is becoming a necessity. It minimizes the attack surface and reduces the chances of unauthorized access.
Enhanced Employee Training: Human error remains a significant vulnerability. Regularly updated training programs that include the latest phishing techniques and security best practices are essential. Gamification and interactive sessions can increase engagement and retention of crucial security concepts.
Comprehensive Incident Response Plans: Having a robust incident response plan in place is more critical than ever. This plan should be regularly reviewed and updated to include responses to new and evolving threats. Simulation exercises can help prepare your team for a real-world breach.
By staying informed and proactive, organizations can significantly reduce their risk and ensure resilience against the evolving threats of the digital age.
Conclusion
What Should You Do?
In the face of these evolving threats, it’s not just about the immediate steps you take, but also about fostering a culture of security within your organization. This means going beyond the basics and integrating security awareness into every aspect of your business operations.
There are a number of basic precautions that can and should be taken regarding security, such as regularly training employees on the basics of security, forcing employees to use VPNs on all work-related devices, implementing the latest security software, etc.
However, as the threat of cyberattacks grows, you should also consider more sophisticated measures such as secure WordPress hosting. If you truly want to protect your company, you’re going to want to utilize such techniques as a dynamic web application firewall, chroot user separation, real-time malware scanning, and full restoration processes in the event of a breach.
Moreover, it’s essential to stay ahead of the curve by keeping abreast of the latest cybersecurity trends and threats. This proactive approach can help you anticipate potential vulnerabilities and take preemptive action to mitigate risks.
When it comes to web security, don’t settle for half-measures. When they fail, the costs are enormous, and you’re left to pick up the pieces.

Great article