We’ve all been enjoying the benefits of WordPress’s popularity. We’re surrounded by beautiful themes, high-powered plugins, and helpful communities. But there’s a dark side to that popularity – it makes WordPress sites an ideal target for hackers around the world.
Before going any further, let’s get one thing straight: WordPress, as a site, is secure.
But … WordPress is not always secure when it’s used improperly by human beings.
So if you want to keep your WordPress site safe, you need to follow some basic WordPress security best practices. In this post, I’ll discuss some simple WordPress security tips that everyone can, and should, apply to their WordPress site.
Then, I’ll dig into a few more advanced tweaks you can make to secure WordPress. But let’s start with the easy things first!
If you do nothing else, following these three simple security tips will already make your WordPress site more secure than most other WordPress installs.
Use a Respected Security Plugin

I’ll get into some smaller security tweaks later on. But this one of the most important WordPress security tips to follow.
If you use a quality security plugin, it will automatically take care of many of the security tweaks required to bolster WordPress’s defenses. Some good options are:
Pick one, install it, and keep it updated. On that note …
Keep Everything Updated. At All Times. No Matter What. Seriously.
Updating your WordPress software, plugins, and themes is one of the simplest things you can do to keep your site safe … yet so many WordPress users ignore this practice. For example, in February a WordPress REST API Vulnerability resulted in the defacement of hundreds of thousands of WordPress installs.
But had site owners immediately updated to WordPress 4.7.2 when it was released, the vulnerability would not have been a problem.
And it’s not just the core software – plugin vulnerabilities can also sink your site. Sucuri found that 25% of hacked WordPress sites were exploited because they ran out of date versions of one of just three popular plugins.
All that to say, keep your WordPress site updated. If you don’t want to handle it manually, Pagely’s managed WordPress hosting automatically keeps your WordPress core and plugins up to date, with a healthy dose of additional security protections.
Back Up Your Site Regularly (And Store Backups Safely)
All the security hardening in the world won’t help you restore your site if something goes belly up. That’s why regular backups are still an absolute must.
Some plugin options for backups are:
If you host with Pagely, you can also take advantage of automatic daily backups pushed directly to your Amazon S3 account.
With any backup, you need to make sure to follow backup best practices. I’m a fan of the 3-2-1 method. Keep three total backup copies, with two of them stored locally, and one stored remotely.
And Now 8 More “Not So Simple” WordPress Security Tips
These tips can further harden your WordPress site’s security but may require digging into code or other more advanced tweaks.
Lock Down Your Login Page
One common way hackers will get into your site is brute force attacks. In other words, they repeatedly try to guess your password. Of course, step one is to use a username/password combination that’s hard to guess – no “password123,” please.
But another way to fight back is by locking down your login page. A few methods to combat brute force attacks are:
- Two-factor authentication
- Limiting login attempts. A plugin like Login LockDown can help.
- Moving the login page.
Follow Principle of Least Privilege
The principle of least privilege is just a fancy way of saying, “don’t give your users more power than they need.” For example, if you’re creating a WordPress user account for someone to contribute blog posts to your site, that person certainly does not need access to add new plugins.
Brush up on WordPress user role capabilities and only dole out accounts with as few privileges as needed. And once those privileges are no longer needed, make sure to remove access.
Use an SSL Certificate
SSL certificates aren’t just for eCommerce stores – they secure your site for everyone, which is a major reason why Google has been pushing so hard for their adoption.
Using SSL ensures that if you, say, log in to your WordPress dashboard over public Wi-Fi at the airport, hackers won’t be able to sniff out your login details. And it will similarly protect every other user with an account at your site.
Free services like Let’s Encrypt make it simple to implement SSL, so there’s no reason not to take advantage. Just make sure you properly set up 301 redirects and move all your assets to HTTPS to prevent man-in-the-middle attacks.
Keep an Audit Log
An audit log is basically a virtual paper trail of every single change that happens on your WordPress site. It won’t actively prevent malicious activity, but it can help you root it out before it balloons into something much larger.
For example, an audit log could alert you to the fact that one of your user accounts is acting suspiciously, allowing you to take action before any permanent damage can be done.
WP Security Audit Log is a great option for tracking what’s happening on your WordPress site.
Don’t Use the Default Database Prefix
Changing your database prefix from the default “wp_” helps add some simple “security by obscurity” to your site.
If you’re freshly installing WordPress, you can choose a custom database prefix during that process. Similarly, most auto-installers generate random prefixes nowadays.
Disable File Editing
By default, some user roles can edit theme and plugin files directly from the WordPress dashboard. That means if an unauthorized user ever gets access to a user account with the proper use role (following the principle of least privilege should make this harder!), they can inject their own code into your site.
To remove this ability, you should disable file editing from within the WordPress dashboard. To do that, you just need to add the following code to your wp-config.php file:
## Disable Editing in Dashboard
define('DISALLOW_FILE_EDIT', true);
Use the Correct File Permissions
File permissions define what actions people can apply to the files on your server. You should never set any WordPress file or directory to 777 permissions.
Instead, make sure your permission scheme is as follows:
- Folders – 755
- Files – 644
Disable Pingbacks
WordPress pingbacks are enabled by default. But for most sites, they offer little benefit. Instead, they can be used to turn your WordPress site into an unwilling participant in a DDoS botnet.
To turn off pingbacks, you can go to “Settings –> Discussion” and uncheck the “Attempt to notify any blogs linked to from the article” box. It’s also a good idea to uncheck the “Allow link notifications from other blogs (pingbacks and trackbacks) on new articles” box:
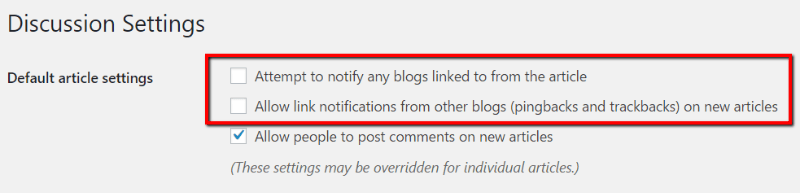
You can also use a plugin like Disable XML-RPC to accomplish the same effect.
Every year, hundreds of thousands of WordPress sites get hacked. By implementing these WordPress security tips, you can ensure your WordPress site doesn’t join that unfortunate list.
And if you want to learn more about how your web host can help keep your WordPress site safe, read Pagely’s approach to secure WordPress hosting.

Here are a few more 🙂
i) Remove unutilized or underutilized themes and plugins. Many attacks against a theme or plugin do not require them to be active on the site, the attacker can hit the plugin/theme files directly to successfully exploit your site(s). “underutilized” means, maybe find a simpiler theme or plugin that does a sufficient job, with less moving parts means less risk of exploits being found.
ii) Choose strong passwords, better yet add a two-factor authentication plugin! No reason to let them in the front door.
iii) Do not log in from unsecured or public wifi hotspots. Unfortunately, session replay attacks are a valid threat against WordPress installations, that blog post can wait. The only prevention for this is to enable SSL for the site, or just not log in from untrusted networks.
iv) Know when to decommision a site. It’s hard to pull the plug on something you worked on, but in the end, if you don’t find yourself with enough time to write a few posts or market your site … it might just be time to let it finalize. It’s better than leaving the site up, and allowing it to be utilized by someone with malicious intent after it’s been compromised.