There’s no nice way to put this, so I’m just going to come out and say it: WordPress websites are prime targets for hackers. It’s not that WordPress itself is an inherently unsafe content management system. In fact, I would go so far as to say that the WordPress security team does a fantastic job in developing a secure platform as well as maintaining a strategy for it.
That said, WordPress is a lot like Scarlett Johansson. Both are perceived as sleek, smart, professional, and reliable entities within their given niches. And they both continue to churn out big successes that earn them rave reviews. (ScarJo currently participates in the Avengers movie series whereas WordPress hosts some of the most high-profile websites around the world.)
But with all that good work and a solid reputation to back it up, both have become easy targets for people wanting to do them harm. For ScarJo, it was an unfortunate breach of privacy when someone leaked sensitive photos of her on the web. For WordPress, well, it’s had its share of security breaches over the years.
There is a reason why WordPress is so popular.
The content management system performs consistently well for its users and makes it possible for companies of all sizes to sufficiently conduct business online. The matter of WordPress security shouldn’t be called into question at this point, particularly with such robust security options including in managed WordPress hosting.
What we need to focus on is getting its users to do the right thing and take responsibility for protecting their instances.
WordPress Security: A Brief History of Exploits and Vulnerabilities
You’ve come here because you’re wondering if WordPress is safe enough to run your online business from. And the answer to that is “Yes!” however…
There is always a “but” or “however” whenever we talk about securing a business’s assets. Think about it like this:
You have a license that allows you to rent office space and conduct business in your city. You also own the domain name that enables you to do business online. But just as the physical location of your operations requires extra fortification–e.g. surveillance systems, security desks, restricted access privileges, business insurance, and so on–so too does your online location.
Personally, I think concerns over WordPress security are a bit overblown. I’m not trying to diminish the severity of security breaches that have hit WordPress servers. However, if you look at how quickly each was resolved as well as the circumstances surrounding how those exploits actually ended up on websites in the first place, you’ll see that the fault doesn’t always lie with the CMS. In fact, many of the issues stem from the things we add to it.
To demonstrate my point, here are some examples of high profile security exploits and vulnerabilities that have appeared over the last decade:
The Slider Revolution Plugin Problems
As noted in this paper by Security Affairs, the Slider Revolution (RevSlider) plugin has had its fair share of security issues. On more than one occasion, hackers have used the plugin to gain entry into WordPress websites for the purposes of installing malware.
One of the things that complicated this specific security exploit was the fact that a number of commonly used WordPress themes included the RevSlider. So, even if users who had installed the plugin issued the patch and followed the recommended security protocols, users who received the plugin through their theme might not have known to do the same (unless the theme developer tipped them off to it).
The Panama Papers Breach
The Panama Papers hackers didn’t strictly exploit a known security weakness in WordPress in order to obtain sensitive data from Mossack Fonseca (MF). However, what they were able to extract through WordPress turned out to be quite valuable. And guess how they were able to get through?
The Slider Revolution plugin.
In all fairness, the law firm was to blame for this particular breach as it was determined that hackers exploited a vulnerability in an older version of the plugin. Because the persons responsible for maintaining the MF website hadn’t updated the plugin to the latest version, their website was left wide open to attack.
The 2015 Mass Plugin Coding Error
This was related to the WordPress Codex. What happened was this:
- The Codex published information on how to use two functions when building a WordPress plugin.
- The instructions provided were not clearly stated, which led to a number of developers actively introducing a vulnerability that left their customers’ sites open to a cross-site scripting attack.
- The plugins affected weren’t a bunch of unknowns either. Many of Automattic’s own plugins were part of the mass contamination.
Once the error was noted, WordPress worked in conjunction with the developers of all affected plugins to fix the error and issue a patch immediately to all users. All other developers were put on high alert to check their plugins and fix the erroneous code.
The TimThumb Image Resizing Tool Wreaks Havoc in Themes
TimThumb was an image resizing script used within a number of WordPress themes. Of course, this was around the time when responsive web design started to take center stage in discussions around web design and so it makes sense that theme developers would want to use a tool that simplified the process for resizing images.
Nevertheless, no one originally thought to look into how TimThumb worked despite how pervasively it was used in WordPress themes. Basically, it hooked directly into the WordPress database and gave anyone unwarranted access to the backend of many websites. Because of this, hackers could inject malicious code without having to do much work to breach a site.
As of today, TimThumb no longer exists–and it’s because of how much damage this tiny script had the potential to bring to so many websites.
The WordPress REST API Vulnerability
This is a big one and it occurred quite recently, too.
When WordPress introduced the REST API, it was meant to open up the content management system in a huge way for web developers:
“Our imagination is the only limit to what can be done with the WordPress REST API. The bottom line is, if you want a structured, extensible, and simple way to get data in and out of WordPress over HTTP, you probably want to use the REST API.”
However, there was a bug introduced with the REST API that allowed anyone to add, change, or delete content on any WordPress website. When the vulnerability was discovered, WordPress worked to patch the bug and silently issued it out to users. While that was all well and good, thousands of users had yet to issue the patch long afterward.
What Can WordPress Users Do to Secure Their Websites?
WordPress is not typically a breeding ground for security exploits. When it or any of its contributing developers, have been guilty of introducing vulnerabilities into the system, they are fixed swiftly. However, without the active participation of WordPress users to protect their websites from external threats, WordPress might never really have a chance to be seen as a 100% secure content management system (do such a thing really exist?).
So, I want to talk next about what you can do to successfully run your business from WordPress and keep it safe in the process.
Step 1: Understand the Threats
To talk about threats to WordPress security, we need to look at this from two angles. The first is from the perspective of what exactly within WordPress allows the intruding presence in. The second is on the kinds of malicious injections your site may be vulnerable to.
Inside WordPress
In 2016, Wordfence reported that roughly 56% of all hacked WordPress websites stemmed from a plugin.
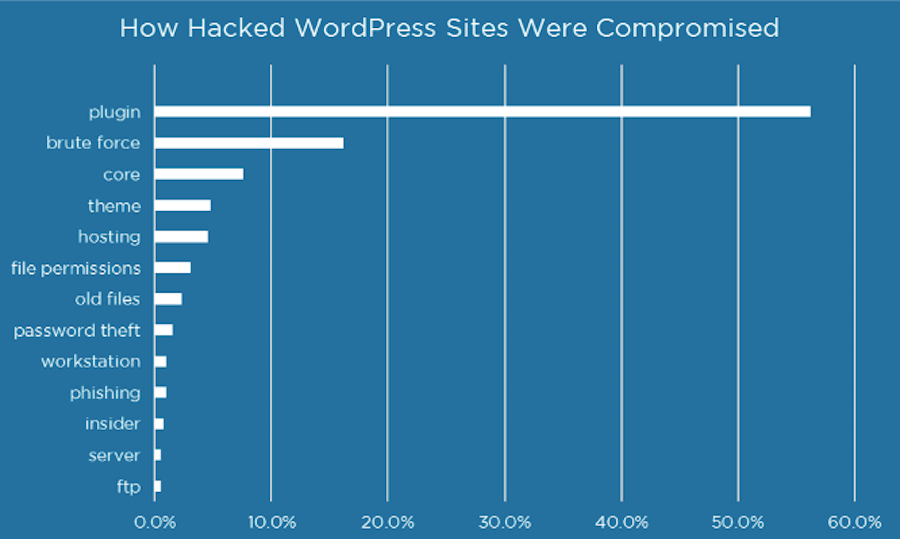
Over a year later, a study of WPScan’s Vulnerability Database found WordPress plugins to still be the prime suspect in WordPress security breaches, being responsible for 54% of all vulnerabilities detected.
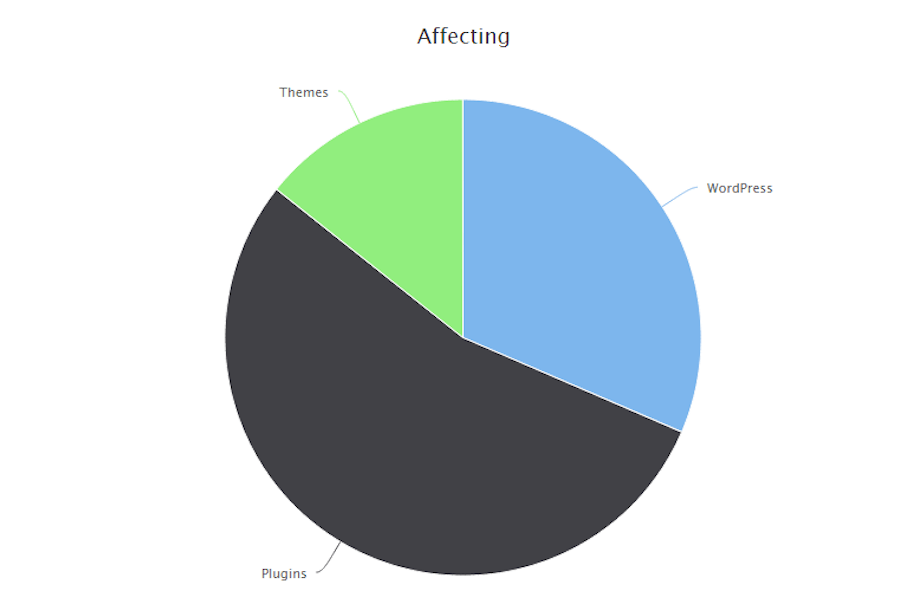
As you can see from the data, WordPress plugins aren’t the only way hackers and bots are breaking their way into websites. Brute force attacks on the login are the second most common form of attack. Followed by WordPress core and theme vulnerabilities.
Outside WordPress
On the other side of this are the kinds of attacks that target your files, the point of entry, plugins, themes, and other vulnerable spots in WordPress. Familiarize yourself with the most common types of security breaches so you’ll know how to spot them when they happen.
According to this 2016 Wordfence report, these are the types of actions hackers take once they’re inside WordPress:
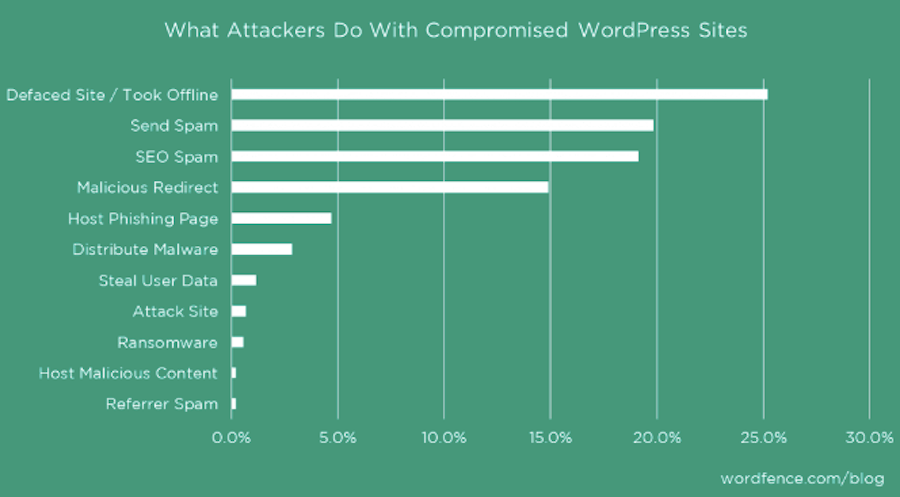
You may be surprised to see that most hackers aren’t looking to steal your customer’s or business’s data. Instead, a lot of their actions are motivated by harming a website’s reputation (through defacement or pulling a site down altogether) or by using it as a vehicle to infect others (through spam, phishing, and malware, among other tactics).
Understanding the vulnerabilities of WordPress and what hackers are looking for is only the first step. Now, let’s look at how you can raise your defenses.
Step 2: Put up a Defensive Line
It’s not enough to install a plugin and call it a day–especially as we’ve seen in the high-profile cases of security breaches mentioned above. To properly defend a WordPress website requires a multi-pronged approach. Everything from your server to your customer’s data needs to be vigorously defended from attack.
Here are the 11 things that need to be part of your WordPress security strategy going forward:
1. Use Secure Hosting

Before you do anything else, make sure your web hosting plan has you covered. This translates to features like:
- Datacenter security measures, including surveillance
- Avoiding shared hosting plans, as you can’t mitigate security breaches from other sites that share your node
- Server-side security architecture that includes a firewall and anti-malware software
- SSL certificate add-on
- Automated or managed backups
- Managed updates
Even better is to sign up for a secure WordPress hosting plan, so you can have experts handle some of the security measures I’m about to discuss for you.
2. Install an SSL Certificate
For those of you who already have a website up and running, and it’s still sitting on HTTP, get yourself an SSL certificate. This certificate puts an extra encrypted buffer between your server and all others, which is why Google rewards HTTPS websites with higher rankings.
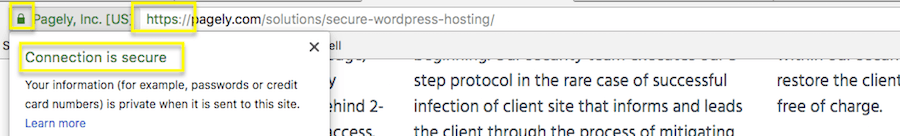
Not only that, but Google also slaps a “Secure” label onto HTTPS web addresses to let visitors know when they’re on a website that has this extra level of protection installed.
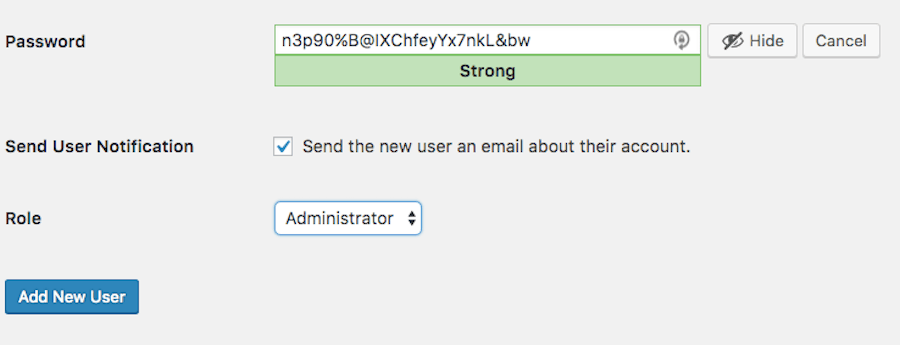
3. Remove Default Admin Username and Login
With every new WordPress installation, you will be granted an “admin” username. Under no circumstances should you use this username. In fact, you should delete it completely. However, before you do, you must create a new admin user to replace it. Give yourself (or whoever the admin superuser is) a unique name. Then use WordPress’s password generator tool to come up with a complex password.
I would also suggest changing the login URL for your WordPress site. By default, WordPress will be located at something like:
https://thisisyoursite.com/wp-admin/
Or:
https://thisisyourothersite.com/wp-login.php
Personally, I like to use a plugin to do this. Ideally, it’s one that handles other security protocols for you like All in One WP Security & Firewall. With one quick switch, you can rename (and essentially hide) the main login page.
4. Hide WordPress Identifiers
Remember how I mentioned earlier that hackers can get into websites if users haven’t updated their software to the latest and most secure versions? Part of the reason this is even possible is because hackers can easily track down websites running on outdated versions of WordPress or using themes with known vulnerabilities.
Rather than leave that data out in the open for hackers to discover and exploit, take steps to hide it.
You can hide your WordPress version by enabling that feature in your security plugin (like Wordfence).

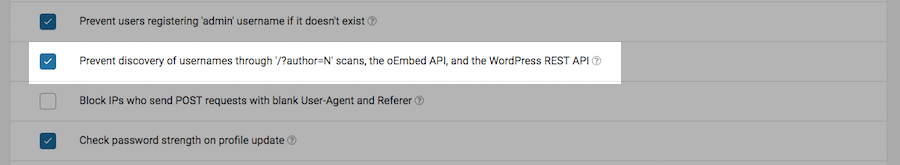
You should also prevent others from discovering the list of usernames associated with your website (it’ll make it all the more difficult for brute force attacks to take place):
If you want to hide the name of your theme, you have a couple of options.
The first is to look within the Theme Customizer to see if it’s easy enough to switch off. It should be in the Footer section. If not, you can edit the footer.php document on your site. There should be a section dedicated to “site-info”. By deleting this, you’ll remove the line at the bottom of the site that says what your site was made with. WPBeginner has a quick tutorial that will show you how to do this.
5. Install a Security Plugin
I’ve already mentioned a couple of different security plugins and how they can help fortify certain parts of your WordPress site. These kinds of plugins are also helpful in terms of providing:
- A firewall
- Malware monitoring and protection
- DDoS scanner and protection
- IP blacklisting and whitelisting capabilities
- Geography-based blacklisting
- Enforcement of stricter password standards
- Enabling two-factor authentication
- Monitoring of database, themes, and plugins for changes to files
If you can, find yourself a WordPress security plugin that covers all these bases and more. As I’ll mention a few points down, the fewer plugins you have installed on your system, the better. So, for all-in-one security solutions in WordPress, I’d recommend the following:
6. Install Akismet
The Akismet Anti-Spam plugin is such a simple one in terms of what it does. Yet, it can save your site as well as your blog readers from a whole lot of trouble by blocking malicious users from leaving comments that contain corrupt links within them.
7. Be Selective with Plugins and Themes
In general, themes and plugins are just plain awesome. They decrease the amount of work you have to do from-scratch while also allowing you to quickly adopt newer design techniques that might otherwise take a while to master through coding. However, some WordPress themes and plugins need to be avoided.
So, here’s what I would suggest:
- Always fully vet any WordPress theme or plugin before you install it.
- Use only what you need. To start, install the enterprise plugin essentials. You can add more as you find a need for them.
- Subscribe to the Wordfence security reports. They list out the top themes and plugins that were most susceptible to security breaches. They also will often draw attention to fake plugins and themes created for the purposes of infiltrating websites.
Also, once you’re done with an old theme or plugin, get rid of it. Don’t just deactivate it on the off-chance you might want to use it again in the future. Delete it entirely from your site. This’ll free up storage, bandwidth, and also reduce the chances that a breach in that theme or plugin leads a hacker straight to you.
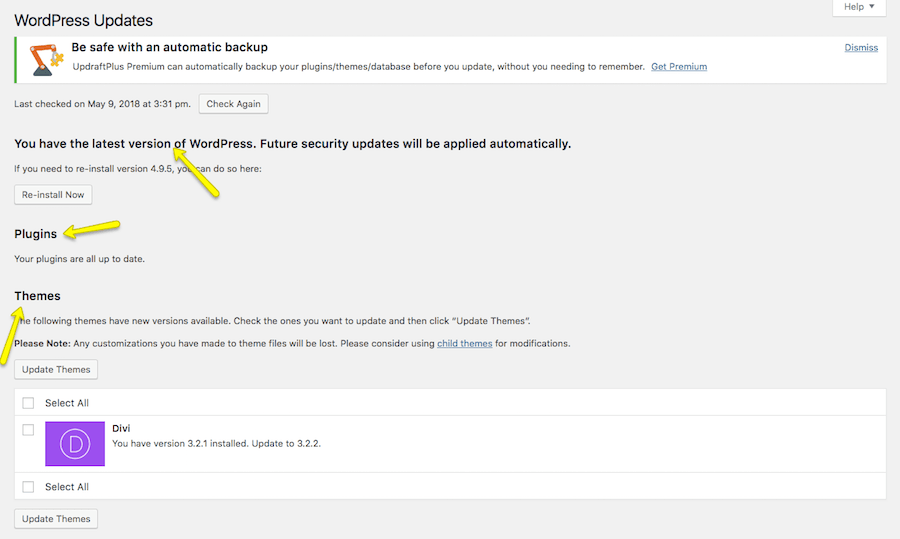
8. Keep Everything Updated
Outdated software is too often the reason why WordPress websites get hacked. There is a reason why WordPress sends you a notification whenever a new version of the core, your theme, or plugins are available.
Generally, it’s best to perform the update on a test version of your website. That way, if a new update creates a conflict with something else, you see the white screen of death, and your site goes down, as a result, you can save yourself the trouble of mistakenly issuing that update to the live site.
There are, of course, less severe issues that can happen when you update your WordPress software, too. Take, for instance, WooCommerce 3.3. This update had its users very excited. However, upon installation, many discovered that it created an issue with certain themes. Not a huge problem, but it was enough for WordPress to remove the version from the repository.
So, while you do need to keep everything updated–especially when security updates are issued–be careful in how you apply them to your site.
9. Generate Backups
On a related note, you should have a system for generating regular backups of your WordPress site. In so doing, you’ll have a way to instantly roll your site back to a recent version in case it gets pulled offline by a hacker or, as I just noted, a new plugin or update wreaks havoc on it.
Many premium hosting plans–especially from managed WordPress hosts–will handle this for you. (They’ll also handle WordPress updates, too!) If your hosting plan includes backups, take advantage of it and skip using a non-recommended plugin.
10. Restrict User Access
The nice thing about a security plugin is that it will usually alert you to login activity with your admin users. (You can also watch what others do, too, but that might be overkill.) The reason I say this though is because, realistically, your site shouldn’t have more than a few admins. Everyone else should have restricted access to WordPress. So, being able to watch over your admins can tip you off in case something odd is going down.
Also, by giving each user role a custom WordPress dashboard, by blocking certain users from accessing plugins and themes, by changing read/write permissions based on what they actually need to do, you can ensure that even once inside, a hacker can’t do much.
The easiest way to restrict user access is to use a plugin like User Role Editor that allows you to create custom rules for each role and block certain parts of WordPress based on them.
I would also recommend you be mindful of your WordPress users. Say, for instance, an employee or contractor was recently terminated. Just as you would change passwords that allow them access to company software, you would want to do the same in WordPress. However, there’s really no benefit in saving the username unless they were an author you want to continue attributing content to. Otherwise, delete them completely from the system to prevent their login credentials from ever becoming compromised.
11. Don’t Store Sensitive Data in WordPress
Whether you use your WordPress site to collect leads or to generate sales, all that information needs to go somewhere. If you have the ability to do so, do not store that information inside of WordPress. You’re basically just begging hackers to steal it from you.
Instead, sign up with a secure third-party system that’s been developed to store and protect this kind of information. For lead generation efforts, this means using a trusted customer relationship management (CRM) system like:
For sales, you will need a PCI compliant payment gateway to process your payments. If you’re using WooCommerce to sell your services or goods, use one that seamlessly integrates into your store. My favorites are:
By automating the collection of lead and customer data through these methods, you’re also cutting down on the amount of time you’d otherwise spend managing them manually. I consider that a win-win.
Step 3: Keep a Watchful Eye
Finally, once your WordPress site is as secure as Fort Knox, make sure you have a plan for monitoring it for suspicious activity. WordPress may be secure now, but hackers never stop. They’re always finding new ways to get inside of websites, so you need to be on high alert.
This means watching for the following signs:
- Web traffic has suddenly dropped off.
- Site speed has slowed to a painful crawl.
- Your site doesn’t appear in search results anymore, even when you search for your URL or the name of the site. (Google may have blacklisted the site if that’s the case.)
- Your site is still in search results, but the metadata is all wrong (that’s SEO spam for you…).
- There are new links embedded in your content that you didn’t put there.
- Spammy pop-ups or ads appear on the site.
- Files have been changed in your database though no one on your team made them.
- There’s a huge influx of new users.
- You’re unable to send or receive emails through your website. (You’ll usually discover this when a customer or prospect contacts you through another means to complain.)
- Your homepage has been defaced.
- Your site has gone down completely.
- You can’t log into WordPress anymore.
As soon as these changes have been detected, it’s your job to go into full-on recovery mode. Of course, that depends on what sort of malicious activity took place. However, the first thing to do is check with your web host and WordPress security plugin. These two resources will be able to confirm that a) there was a breach and b) where it occurred. You can then take the necessary steps to remove the malicious activity and re-fortify your website.
Wrapping Up
Look, I realize laying out this robust guide to WordPress security and everything involved in maintaining it might make it seem like a contradicted my original point. And here is what I will say to that:
Whether you use Drupal or Joomla or any other content management system to manage your business’s website, security is going to be a top concern. Hackers have automated the ways in which they target and attack websites through the use of bots and bot networks, and so they’re really not going to discriminate based on which content management system you’re on. WordPress just gets a lot of flack because it’s the most commonly used one.
If you’re finding all of this hubbub around WordPress security to be overwhelming, then secure WordPress hosting with Pagely is probably your best bet. While there are still some parts of the security process you and your team will be responsible for, a managed WordPress host can provide you with a stable base to start from and provide some peace of mind when it comes to keeping your site safe.
